I. Introduction to Open Authorization (OAuth): The Core Framework
Defining OAuth
OAuth (Open Authorization) is an open standard that allows a user to give a third-party application limited access to their online account without sharing their password.
At its core, OAuth is an open standard for secure access delegation. The protocol defines a standardized mechanism through which a client application can obtain limited access to a user’s protected resources from a resource server on behalf of the user, without the user having to expose their password to the client application. This is achieved by exchanging the user’s permission for a temporary, revocable access token. This token acts as a proof of permission and is the only credential the client application ever holds, effectively decoupling the user’s primary login credentials from the third-party service.
Authorization vs. Authentication: A Critical Distinction
A common and critical point of confusion for those new to the protocol is the difference between authorization and authentication. The name “Open Authorization” itself is a precise description of the protocol’s function, not a misnomer.
- Authentication is the process of verifying a user’s identity—the act of proving “who you are.” This is typically accomplished through a login process where a user enters credentials like a username and password.
- Authorization, by contrast, is the process of granting permission to access specific resources or perform specific actions—determining “what you can do”.
OAuth is an authorization framework, not an authentication protocol. It is designed to grant delegated access to resources, not to verify a user’s identity. However, these two processes often work in concert. Protocols like OpenID Connect (OIDC) were developed specifically to address this need by building an identity layer on top of the OAuth 2.0 authorization framework. An application can use OIDC to authenticate a user and simultaneously use OAuth to obtain an access token to the user’s resources. This layered approach allows for a complete, secure identity and access management solution.
The Problem of Shared Credentials: What Happened Without OAuth?
Auth was created to solve a major security problem on the early internet: password sharing.
Before OAuth (around 2007), if you wanted a third-party app (like a photo printing service) to access your data on another platform (like Google Photos), you had to give that app your actual username and password.
This method was risky and inefficient, as it exposed your password and opened the door to serious security issues. OAuth replaced this unsafe practice with a safer way to share access without sharing passwords.
Operational and User Experience Failures
Beyond the security risks, the password-sharing model was a nightmare from a usability and administrative perspective.
- All-or-Nothing Access: The permission model was binary: an application either had complete and unfettered access to a user’s account and could perform any action, or it had no access at all. This fundamental design limitation meant users had no ability to grant fine-grained permissions. An application that only needed to read a user’s contacts might gain access to their private messages, calendar, and friends list, violating the principle of least privilege.
- Administrative Overhead: When a user changed their password on the primary service, every single third-party application that had been granted access would immediately break, requiring the user to re-enter their new credentials. This was an unsustainable model for both users and developers.
- Lack of Standardization: The absence of an open standard meant that major services like Microsoft and Yahoo each had their own proprietary protocol for delegated access. This created a fragmented ecosystem where developers had to learn and implement a different, custom integration for every service they wanted to connect with, a process described as a “nightmare to implement”.
Why OAuth is Needed (Problems It Solves)
Before OAuth, users had to give their actual login credentials (username/password) to every app that wanted access to their data, which is highly insecure. OAuth solves this by:
- No password sharing. The user only logs in at the trusted Authorization Server (e.g. Google). The third-party client never sees the password. For example, you can let a printing service read your Google Photos without ever giving it your Google password.
- Granular, limited permissions. Clients request specific scopes of access (e.g. “read Drive files” or “send Gmail”). The user’s consent and the issued token are limited to those scopes. This least-privilege model means the app gets exactly the permissions needed, and nothing more.
- Tokens, not credentials. Apps store and use opaque access tokens instead of passwords. If a token is stolen or misused, it can be revoked without forcing the user to change their password. As one security guide notes, OAuth “allows applications to access a user’s data without exposing their credentials”, greatly reducing the risk of compromise.
- User control and audit. The user can see and revoke granted tokens (via their Google Account settings), and OAuth’s scoped consent screen informs users precisely what data the app will access.
Versions of OAuth
- OAuth 1.0: Released in 2007 (with a revision in 2010 as OAuth 1.0a), this was the initial version. It uses cryptographic signatures for security, requiring complex calculations for each request. It’s still used in some legacy systems but is less common today due to its complexity.
- OAuth 2.0: Introduced in 2012 (RFC 6749), this is the most widely adopted version. It simplifies the process by using access tokens (often bearer tokens) and supports various grant types (e.g., authorization code, implicit, client credentials). It’s more flexible, supports mobile apps, and relies on HTTPS for security rather than signatures. Extensions like OpenID Connect build on it for identity verification.
- OAuth 2.1: This is an ongoing draft (as of 2025, it’s in development and not yet a formal standard). It aims to consolidate best practices from OAuth 2.0, improving security by deprecating weaker flows (like implicit grant) and mandating features like PKCE (Proof Key for Code Exchange) to prevent certain attacks.
II. The Foundational Architecture of OAuth 2.0
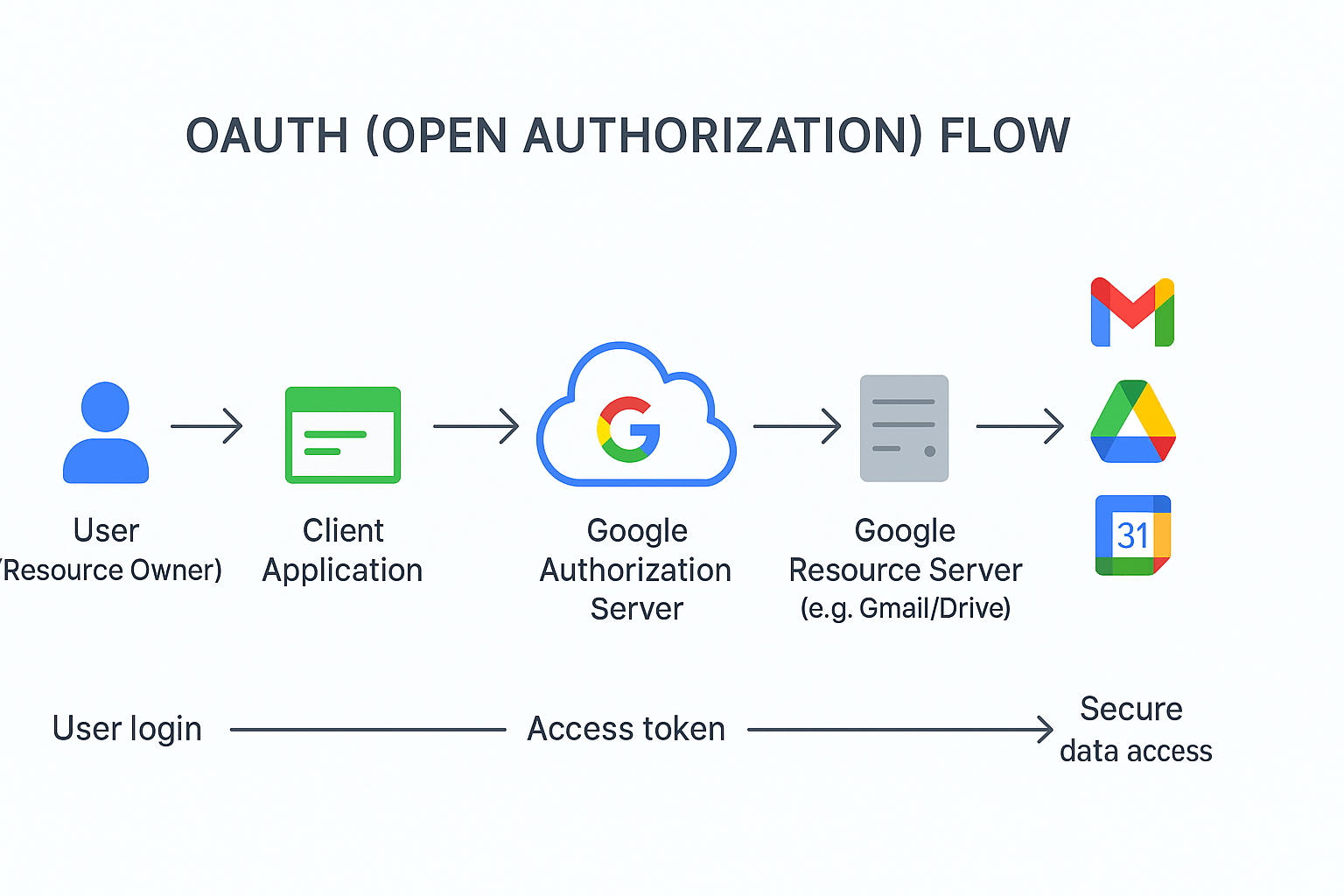
The OAuth 2.0 framework introduces a set of defined roles and components that orchestrate the secure delegation of access. Understanding these roles is crucial to comprehending the protocol’s security model and its implementation.
The Four Principal Roles
The protocol defines four main actors that interact during an OAuth transaction.
- Resource Owner: This is the entity that owns or controls the protected resources. When the resource owner is a person, they are referred to as the end-user. The resource owner is the one who grants permission for a client application to access their resources.
- Client: The client is the application that wants to access the protected resources on behalf of the resource owner. The client can be a mobile application, a web application, a desktop application, or even a service-to-service process.
- Authorization Server: The authorization server is the central component responsible for authenticating the resource owner and, after receiving their consent, issuing an access token to the client.
- Resource Server: The resource server is the API or service that hosts the protected resources. It is responsible for accepting and validating access tokens from the client and providing the requested data.
The following table provides a clear mapping of these abstract roles to a concrete example, such as a third-party application interacting with Google Workspace.
| Role | Description | Example (Google Workspace) |
|---|---|---|
| Resource Owner | The user or entity that owns the protected data and has the ability to grant delegated access. | A Google Workspace user (@your-organization.com) who owns files in Google Drive. |
| Client | The third-party application requesting access to the user’s resources on their behalf. | A productivity app or a web-based document editor that needs to access Google Drive files. |
| Authorization Server | The service responsible for authenticating the user and issuing access tokens. It is the gatekeeper. | The Google OAuth 2.0 server. |
| Resource Server | The API or service that holds the protected resources and responds to requests made with a valid token. | The Google Drive API or the Google Calendar API. |
Key Components of the Flow
Beyond the roles, several key components are fundamental to the OAuth protocol.
- Access Tokens: An access token is a piece of data that represents the authorization granted to a client application to access specific resources. It is a short-lived credential that is used by the client to make API calls to the resource server. The format is not strictly defined by the protocol, but JSON Web Tokens (JWTs) are commonly used.
- Refresh Tokens: To allow for long-term or “offline” access without requiring the user to re-authorize, the authorization server can issue a refresh token along with the access token. A refresh token is a long-lived credential that the client can use to obtain a new, fresh access token after the current one has expired. This is a more secure model than using a single, long-lived access token.
- Scopes: Scopes are a crucial feature of OAuth that solve the all-or-nothing access problem of the pre-OAuth era. They are space-delimited strings that allow the client application to specify exactly what permissions it needs from the user (e.g.,
https://www.googleapis.com/auth/drive.readonlyto only read Google Drive files). This mechanism allows the user to grant granular, least-privilege access, ensuring that an application only accesses the resources it needs to function. - Grant Types: OAuth 2.0 defines various “grant types,” which are the standardized flows for obtaining an access token. These flows are specialized for different types of clients and use cases. The most common and secure flow for web applications is the Authorization Code grant type, while others exist for scenarios like mobile apps (PKCE) or server-to-server interactions (Client Credentials).
III. Evolution of the Protocol: From OAuth 1.0 to OAuth 2.0
The history of OAuth is a story of continuous adaptation to the changing landscape of the internet. The transition from OAuth 1.0 to OAuth 2.0 was not a minor update but a radical redesign that addressed the shortcomings of the original specification.
The Limitations of OAuth 1.0
The first version of the protocol, released in 2007, was a significant step forward as the first open standard for access delegation. However, it was quickly outpaced by the proliferation of new application types.
- Overly Complex Security: OAuth 1.0 required clients to cryptographically sign every request using a shared secret key. While this approach provided strong security, it was “much more complicated” to implement and debug for developers.
- Limited Use Case: The specification was designed primarily for “traditional server-client web applications” and was not flexible enough to support the growing demand for mobile, single-page, and connected device applications.
- Fewer Authorization Flows: OAuth 1.0 was limited to a single standardized flow, which proved to be a major restriction for developers working with a diverse range of clients that did not live in a web browser.
The Radical Redesign of OAuth 2.0
The limitations of version 1.0 led to the complete overhaul of the protocol in 2012. OAuth 2.0 was designed to be simpler, more scalable, and more flexible for a modern, fragmented digital ecosystem.
- Simplified Security Model: OAuth 2.0 “ditched” the complex cryptographic signatures of its predecessor and relies entirely on HTTPS (SSL/TLS) for the security of data in transit. This design choice greatly simplified the implementation process for developers, though it shifted the security burden to the underlying transport protocol.
- Broad Client Support and Multiple Flows: The new specification introduced six different authorization flows (grant types), each tailored to a specific application type, such as web server applications, native mobile apps, or devices without a browser. This flexibility was a key driver for its rapid and broad adoption.
- Improved Token Management: OAuth 2.0 introduced the now-standard practice of using short-lived access tokens and long-lived refresh tokens. This model is considered more secure than the long-lived tokens that were common in OAuth 1.0.
A Comparative Analysis
The table below provides a side-by-side comparison that highlights the strategic differences and trade-offs between the two major versions of the protocol.
| Feature | OAuth 1.0 | OAuth 2.0 |
|---|---|---|
| Complexity | High; required cryptographic signatures on every request. | Lower; simpler to implement by relying on HTTPS for security. |
| Security Model | Based on cryptographic signing of requests. | Relies on HTTPS for security. |
| Client Support | Primarily designed for traditional web applications. | Flexible, supports web, mobile, desktop, and IoT devices. |
| Authorization Flows | Limited to a single, standardized flow. | Offers multiple grant types for different client needs. |
| Token Lifetime | Generally used long-lived access tokens. | Emphasizes short-lived access tokens and refresh tokens. |
IV. Case Study: Implementing OAuth for Google Workspace
To illustrate the principles of OAuth in a practical context, this section will detail the process of a third-party application implementing the Authorization Code grant type to access a Google Workspace user’s data.
Mapping the Roles to Google
The abstract roles of the OAuth framework are given concrete form within the Google ecosystem:
- Resource Owner: A Google Workspace user. Their credentials, managed by their organization, are the basis for all delegated access.
- Client: A third-party application, such as a cloud-based video editor or a project management tool, that wants to access the user’s data. The application must be registered with Google to receive its unique
client_idand, for server-side apps, itsclient_secret.- Authorization Server: The Google OAuth 2.0 authorization endpoint. This is the trusted intermediary that handles user authentication and consent.
- Resource Server: The Google APIs that host the protected resources, such as the Google Drive API, Gmail API, or Calendar API.
The Developer’s Journey: Registration and Configuration
Before a single OAuth flow can be initiated, the developer of the client application must complete a series of preparatory steps within the Google Cloud Console.
- Enable APIs: The developer must enable the specific Google APIs they plan to use for their project (e.g., the Google Drive API).
- Create Credentials: The developer creates an OAuth 2.0 client ID by selecting the appropriate application type (e.g., “Web application,” “Android,” “iOS,” etc.). This process provides the application’s unique
client_idand, for web server applications, aclient_secret. - Configure the OAuth Consent Screen: The developer sets up the consent screen that users will see. This screen displays the application’s name and is where the user will be presented with the requested permissions.
- Define Redirect URIs: The developer must explicitly list the
redirect_uri(or “callback URL”) to which Google will send the user back after the authorization process. These URLs are subject to strict validation rules to prevent malicious redirects that could be used to steal tokens. - Identify Scopes: The developer specifies the precise scopes (permissions) their application needs to function. They must choose the minimum set of permissions necessary to adhere to the principle of least privilege, and they may be required to provide a justification for any sensitive scopes.
Step-by-Step Authorization Code Flow
The Authorization Code flow is the most secure method for web server applications, as it ensures that the sensitive access token is never exposed in the user’s browser. The process involves a series of secure interactions between the user, the client application, and Google’s servers.
| Step | Actor(s) | Description | Example Action (Google Workspace) |
|---|---|---|---|
| 1 | Client Application & User’s Browser | The client application initiates the flow by redirecting the user’s browser to Google’s Authorization Server. The request includes the client’s ID, the redirect URI, and the requested scopes.11 | A user clicks “Connect with Google Drive” on a third-party app. The app redirects the user to https://accounts.google.com/o/oauth2/v2/auth?…. |
| 2 | Authorization Server (Google) & User | The Authorization Server authenticates the user (if they are not already logged in) and displays a consent screen listing the permissions the application is requesting. The user reviews the request and grants consent.6 | Google prompts the user to log in and then shows a screen: “Example App wants to access your Google Drive files. Allow?” The user clicks “Allow.” |
| 3 | Authorization Server (Google) & User’s Browser | Upon successful consent, the Authorization Server redirects the user’s browser back to the pre-registered redirect_uri. The URL includes a temporary, single-use authorization code as a query parameter.11 | The user’s browser is redirected to https://app.example.com/callback?code=4/P7q…. |
| 4 | Client Application (Server-side) & Authorization Server (Google) | The client’s server, upon receiving the authorization code, makes a secure, server-to-server POST request to Google’s token endpoint. This request includes the authorization code, the client’s public client_id, and its confidential client_secret.6 | The app’s server calls https://oauth2.googleapis.com/token and exchanges the code for a token. |
| 5 | Authorization Server (Google) & Client Application (Server-side) | Google’s token endpoint validates the request. If everything is in order, it responds with a JSON object containing a short-lived access token and, if requested, a long-lived refresh token.6 | The app’s server receives the access token, which can now be used for API calls. |
| 6 | Client Application & Resource Server (Google API) | The client application uses the access token to make authenticated API calls to the Resource Server (e.g., the Google Drive API). The API validates the token and responds with the user’s data, as permitted by the original scopes.6 | The app makes a call to the Google Drive API: GET https://www.googleapis.com/drive/v3/files with the access token in the Authorization header. |
V. Conclusion
The foundational principles of OAuth—delegated, scoped, and revocable access—remain essential, even as the landscape of interconnected devices and applications continues to evolve. From web services and mobile apps to emerging agentic AI tools, the need for a secure, standardized mechanism for access delegation is more critical than ever, and OAuth provides the framework to meet that challenge.